Operating Systems Concepts: A Comprehensive Guide
Soft Real-Time Systems:
Deadline Flexibility: Deadlines are important but not absolute. Some deadline misses are acceptable.
Performance Degradation: If deadlines are missed, performance degrades gracefully rather than causing total system failure.
Examples: Multimedia systems, online transaction processing, network data transmission.
Prioritization: Tasks are prioritized, but lower-priority tasks can still run if higher-priority tasks miss their deadlines.
Criticality: Less critical applications where timing is important but not critical to operation.
Error Handling: Can handle occasional delays without significant impact on the system.
Predictability: Less predictable compared to hard real-time systems due to occasional deadline misses.
System Design: Designed to optimize average performance rather than ensuring strict adherence to deadlines.
Use Cases: Suitable for applications where performance is important but not critical, such as video streaming and online games.
Response Time: Response time is a target but not a strict requirement; delays are tolerated within acceptable limits.
Hard Real-Time Systems:
Deadline Strictness: Deadlines are strict and must be met every time; missing a deadline can cause system failure.
Performance Degradation: No graceful degradation; missing a deadline can lead to catastrophic failure.
Examples: Air traffic control systems, medical devices, automotive airbag systems.
Prioritization: Tasks are strictly prioritized; higher-priority tasks must always be completed on time.
Criticality: Used in critical applications where timing is crucial to system operation and safety.
Error Handling: Cannot afford delays; any missed deadline can lead to unacceptable or dangerous outcomes.
Predictability: Highly predictable due to strict adherence to timing constraints.
System Design: Designed to ensure that all tasks meet their deadlines, often through rigorous testing and validation.
Use Cases: Essential for applications where timing is critical, such as embedded systems in aerospace and medical equipment.
Response Time: Response time is a strict requirement; deadlines must always be met without exception.
User Mode and Kernel Mode
User mode and kernel mode are two distinct privilege levels in a computer’s operating system, each with its own set of privileges and access rights. Understanding these modes is crucial for understanding how the operating system manages processes and protects system resources. Here’s a concise explanation:
User Mode:
- In user mode, processes run with restricted privileges, only able to access resources and execute instructions allowed by the operating system.
- User-mode processes cannot directly access hardware or sensitive system resources; they must request access via system calls.
- Most user applications, such as word processors, web browsers, and games, operate in user mode to ensure system stability and security.
- User mode provides a protective barrier between user applications and the kernel, preventing unauthorized access to critical system resources.
Kernel Mode:
- Kernel mode, also known as supervisor mode or privileged mode, is a higher privilege level than user mode.
- The kernel, which is the core of the operating system, runs in kernel mode and has unrestricted access to system resources and hardware.
- Operating system components, device drivers, and critical system services operate in kernel mode to perform tasks that require direct access to hardware and system resources.
- Kernel mode allows privileged operations such as modifying memory management settings, accessing hardware devices directly, and handling system interrupts.
In summary, user mode and kernel mode represent two privilege levels in the operating system hierarchy, with user mode providing restricted access to system resources for user applications, and kernel mode allowing unrestricted access for the operating system kernel and essential system components. The separation between these modes ensures system stability, security, and protection against unauthorized access to critical system resources.
Trap And Interrupt
Trap:
Definition: A trap is a synchronous event caused by a specific instruction executed by the processor.
Cause: Generated intentionally by a program to request a system service or due to an exceptional condition (e.g., divide by zero, invalid memory access).
Origin: Always originates from the running program.
Timing: Occurs at a predictable point in program execution.
Purpose: Often used for system calls and handling specific program errors.
Handling: The processor stops executing the current program, saves the state, and transfers control to a trap handler.
Synchronous Nature: Synchronous with program execution; occurs at the specific point where the condition arises.
Examples: System calls (like file operations), illegal instructions, arithmetic overflow.
Control: Often returns control to the same point in the program after handling (especially for recoverable errors).
Types: Software-generated events within the same process context.
Interrupt:
Definition: An interrupt is an asynchronous event caused by an external event or hardware signal.
Cause: Generated by hardware devices (e.g., I/O devices) to signal that attention is needed or an event has occurred (e.g., timer expiration, input available).
Origin: Can originate from external hardware or internal timers.
Timing: Occurs at unpredictable points in program execution.
Purpose: Used to handle asynchronous events and improve system responsiveness.
Handling: The processor stops executing the current program, saves the state, and transfers control to an interrupt handler.
Asynchronous Nature: Asynchronous with program execution; can occur at any time, independent of the current program state.
Examples: Keyboard input, mouse movement, disk I/O completion, network packet arrival.
Control: Often results in a context switch, potentially changing the executing process.
Types: Hardware-generated events that may involve context switches or task prioritization.
Q. What is virtual memory ? What are the benefits of virtual memory systems ?
Definition: Virtual memory is a memory management technique that provides an”illusio” of a large, continuous memory space to programs by using hardware and software to manage data storage on both physical memory (RAM) and secondary storage (like a hard disk or SSD).
Benefits of Virtual Memory Systems:
Larger Address Space:
- Programs can use more memory than physically available RAM, as virtual memory allows them to address a much larger space.
Isolation and Protection:
- Each process operates in its own virtual address space, providing isolation and protection from other processes, preventing accidental or malicious interference.
Efficient Memory Use:
- Only actively used memory pages are loaded into RAM, while less-used pages are stored on disk, optimizing the use of available physical memory.
Multitasking:
- Allows multiple programs to run simultaneously without worrying about running out of physical memory, as the system can swap data in and out of RAM as needed.
Simplified Programming:
- Programmers can write programs without needing to manage memory allocation and deallocation explicitly, as the operating system handles it transparently.
* Critical section Problem
The critical section represents a portion of code or a block where a process or thread accesses a shared resource, such as a variable, file, or database. It’s a section that needs to be executed in an atomic or mutually exclusive manner. To maintain data integrity and avoid conflicts, only one process or thread should be allowed to enter the critical section at a time. This ensures that no two processes interfere with each other and modify shared resources simultaneously, preventing inconsistencies or incorrect results.
Q. What is a page fault? What steps are taken by the OS to handle page faults?
Definition: A page fault occurs when a program tries to access a page of memory that is not currently loaded into the physical RAM. This triggers an interrupt, prompting the operating system to handle the missing data.
Steps Taken by the OS to Handle Page Faults:
Interrupt Triggered:
- The CPU detects the page fault and triggers a page fault interrupt, pausing the current execution.
Determine Cause:
- The operating system checks the memory management unit (MMU) to determine the cause of the page fault, such as whether the page is valid but not in RAM or if it’s an illegal access.
Locate Data:
- If the page is valid but simply not in RAM, the OS locates the required data on the disk (usually in a swap file or paging file).
Select a Victim Page:
- The OS selects a page to evict from RAM if there isn’t enough free space. This involves using a page replacement algorithm (like LRU – Least Recently Used).
Update Page Tables:
- The OS updates the page table to mark the evicted page as not present in RAM and maps the new page to a frame in RAM.
Load Page:
- The OS reads the required page from disk into the now free frame in RAM.
Resume Execution:
- The program’s state is updated to reflect the new page location, and the interrupted instruction is restarted, allowing the program to continue execution.
System Call And Types
System calls are essential functions provided by the operating system that allow user-level processes to request services from the kernel. These calls serve as an interface between user programs and the operating system, enabling processes to perform privileged tasks. System calls can be categorized into several types, each serving specific purposes:
Process Control:
- System calls like
fork(),exec(),exit(), andwait()manage processes by creating, replacing, terminating, and controlling process execution.
- System calls like
File Management:
- Functions such as
open(),read(),write(), andclose()handle file operations like opening, reading from, writing to, and closing files.
- Functions such as
Device Management:
- System calls like
read(),write(), andioctl()control I/O devices such as disks and printers, facilitating data transfer and device configuration.
- System calls like
Information Maintenance:
- Calls like
getpid(),getuid(), andgettimeofday()provide access to system information like process IDs, user IDs, and current time.
- Calls like
Communication:
- Communication system calls like
pipe(),shmget(), andshmat()facilitate inter-process communication and synchronization..
- Communication system calls like
Difference between Paging and Segmentation
Paging:
Basic Concept:
- Memory is divided into fixed-size units called pages.
- Physical memory is divided into blocks of the same size called frames.
- Page size is typically a power of 2, such as 4KB.
- Each process is divided into pages, which are mapped to physical frames.
Address Translation:
- Logical address is divided into a page number and an offset within the page.
- Page number indexes into the page table to get the frame number.
- Frame number combined with the offset gives the physical address.
Fragmentation:
- Suffers from internal fragmentation as the last page may not be completely used.
- No external fragmentation since all pages and frames are of fixed size.
Protection and Sharing:
- Simplified protection mechanism via page tables.
- Pages can have different permissions set in the page table entries.
- Pages can be shared by mapping them into the page tables of different processes.
Flexibility and Complexity:
- Straightforward to implement due to fixed-size pages.
- Less flexible in handling different sized data structures and objects.
Performance:
- Generally better performance due to fixed-size pages and simpler management.
- Page table lookups can be accelerated with hardware support like Translation Lookaside Buffers (TLBs).
Usage Scenarios:
- Widely used in modern operating systems for efficient memory management.
- Common in systems requiring fast and predictable memory allocation.
Segmentation:
Basic Concept:
- Memory is divided into variable-size units called segments.
- Each segment represents a logical unit such as a function, object, or data array.
- Segments vary in length, reflecting the logical divisions within a process.
Address Translation:
- Logical address consists of a segment number and an offset within the segment.
- Segment number indexes into the segment table to get the base address and limit.
- Base address plus the offset gives the physical address.
Fragmentation:
- Suffers from external fragmentation because segments are of variable length and can leave gaps.
- No internal fragmentation within the segments.
Protection and Sharing:
- More intuitive protection mechanisms at the segment level.
- Each segment can have different access rights, enhancing security.
- Segments can be shared between processes, facilitating modular programming.
Flexibility and Complexity:
- More flexible as it handles varying sized data structures and maps logical divisions directly.
- More complex due to the need to manage variable-sized segments and external fragmentation.
Performance:
- Can lead to performance issues due to managing and coalescing free segments.
- Segment table lookups are more complex and might not be as efficiently supported by hardware.
Usage Scenarios:
- Used in systems where logical divisions are important, such as real-time and embedded systems.
- Useful in programming environments prioritizing modularity and data protection.
Process Control Block (PCB)
A Process Control Block (PCB) is a data structure used by the operating system to store all the information about a process. It is essential for process management and allows the operating system to efficiently switch between processes (context switching) and manage the execution of processes.
Components of a PCB
Process Identification (PID):
– Unique identifier for each process.
– Helps in distinguishing between different processes.
Process State:
– Indicates the current state of the process (e.g., running, waiting, ready, terminated).
– Helps the operating system manage the process lifecycle.
Program Counter (PC):
– Contains the address of the next instruction to be executed for the process.
– Critical for resuming the process after a context switch.
CPU Registers:
– Stores the contents of all CPU registers for the process.
– Necessary for restoring the process state during context switching.
Memory Management Information:
– Includes base and limit registers, page tables, or segment tables.
– Helps in managing the process’s memory allocation.
Accounting Information:
– Stores information like CPU usage, execution time, process ID, and user ID.
– Useful for resource allocation and process scheduling.
I/O Status Information:
– Tracks the list of I/O devices allocated to the process, open files, and I/O operations in progress.
– Essential for managing I/O resources and operations.
Process Priority:
– Indicates the priority level of the process.
– Used by the scheduler to determine the order of process execution.
List of Open Files:
– Contains references to all files the process has opened.
– Helps in managing file access and ensuring proper file handling.
Process Privileges:
– Indicates the privileges and access rights of the process.
– Ensures security and access control within the system.
Process Context:
– Encompasses the complete state of the process, including CPU state, memory state, and I/O state.
– Essential for accurately saving and restoring the process state during context switches.
Difference between Single-Threaded and Multi-Threaded Processes
Single-Threaded Process: A single-threaded process has only one thread of execution. This means the process executes a single sequence of instructions at a time. If the thread encounters a blocking operation, the entire process will be halted until the operation completes.
Multi-Threaded Process: A multi-threaded process has multiple threads of execution. This allows the process to perform multiple tasks concurrently within the same process context. If one thread is blocked, other threads can continue executing, improving the process’s overall efficiency and responsiveness.
Key Differences
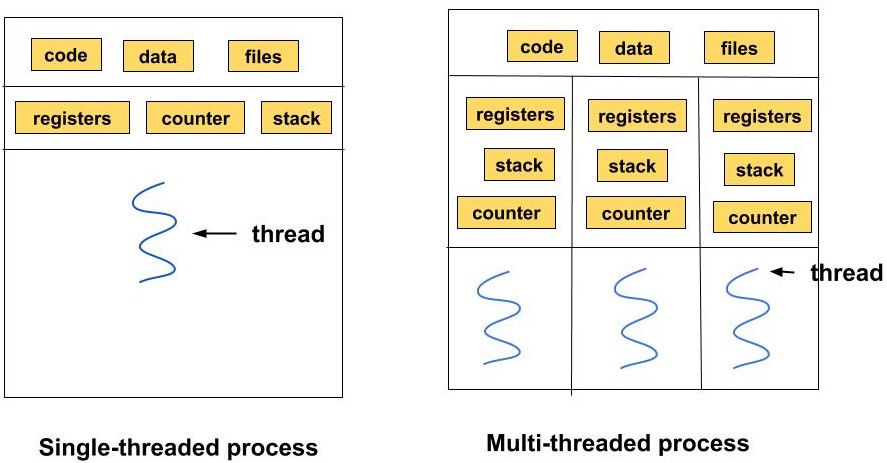
Execution:
- Single-Threaded: Executes one task at a time.
- Multi-Threaded: Can execute multiple tasks simultaneously.
Responsiveness:
- Single-Threaded: Less responsive, as a blocking operation halts the entire process.
- Multi-Threaded: More responsive, as other threads can continue to execute even if one is blocked.
Resource Utilization:
- Single-Threaded: Utilizes only one core/CPU at a time.
- Multi-Threaded: Can utilize multiple cores/CPUs, leading to better performance on multi-core systems.
Complexity:
- Single-Threaded: Simpler to design and manage.
- Multi-Threaded: More complex due to the need for synchronization mechanisms to avoid issues like race conditions and deadlocks.
Concurrency:
- Single-Threaded: No true concurrency, only sequential execution.
- Multi-Threaded: True concurrency within the same process.
Memory Fragmentation and Its Types
Memory fragmentation refers to the phenomenon where available memory becomes divided into small, non-contiguous blocks, making it challenging to allocate large contiguous blocks of memory, which can lead to inefficient memory utilization. Here’s a brief explanation along with its types:
Internal Fragmentation:
- Internal fragmentation occurs when allocated memory blocks are larger than necessary, resulting in wasted memory within each block.
- This type of fragmentation typically occurs in memory allocation schemes where fixed-size memory blocks are allocated, leading to unused space within allocated blocks.
External Fragmentation:
- External fragmentation occurs when free memory exists, but it is dispersed in small, non-contiguous chunks, making it challenging to allocate large contiguous blocks of memory.
- It arises due to the allocation and deallocation of variable-sized memory blocks over time, leaving gaps of unused memory between allocated blocks.
- External fragmentation can hinder memory allocation requests, even if the total amount of free memory is sufficient, leading to inefficient memory utilization.
Implications of Memory Fragmentation:
Reduced Memory Utilization: Fragmentation leads to wasted memory space, diminishing the overall efficiency of memory utilization.
Performance Degradation: Fragmentation can impact system performance, particularly in memory-intensive applications, due to increased allocation and deallocation times.
Strategies to Reduce Fragmentation:
Compaction: Periodically rearranging memory to eliminate fragmentation by moving allocated blocks and consolidating free memory.
Dynamic Memory Allocation: Utilizing dynamic memory allocation algorithms that can adaptively allocate variable-sized memory blocks to reduce internal fragmentation.
1-Soft Real-Time Systems, Hard Real-Time Systems
2-Message Passing Model, Shared Memory Model
3-Trap, Interrupt
4-Virtual memory, Critical section Problem
5-Page Fault
6-System Call and types
7-8-Difference between Paging and Segmentation
9-Process Control Block (PCB)
10-Difference between Single-Threaded and Multi-Threaded Processes
